legoを使ってLet’s EncryptのSSL証明書をDNS認証で発行しFileMaker Serverに設定する方法
Let’s EncryptのクライアントでlegoというCLIツールがあります。
Go製のCLIツールのため、導入や実行が簡単にできます。
非常に簡単に実行できたので、タイトルのとおり、FileMaker Serverに設定する方法を紹介します。
当然ですが、すべて自己責任にてお願いいたします。
環境など
今回は、以下の環境で作業をしました。
- Windows Server 2016
- FileMaker Server 17
- lego v2.1.0
DNSのコンパネにログインして、TXTレコードを編集できる必要があります。
まずはlegoをダウンロードする
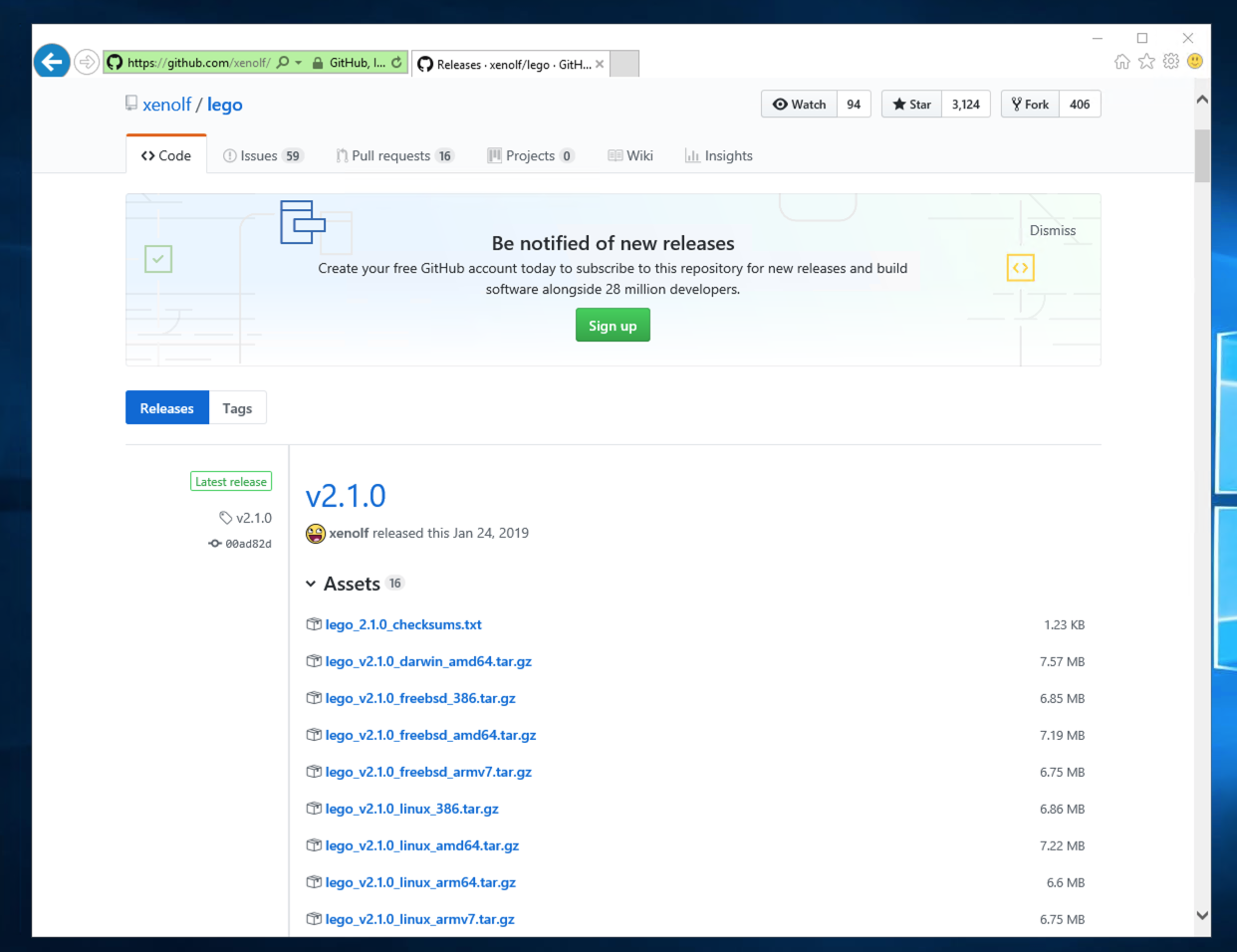
GitHubのリリースからダウンロードします。
legoのリポジトリはこちら
https://github.com/xenolf/lego
ダウンロードはこちら
https://github.com/xenolf/lego/releases
以下をダウンロードします。
lego_v2.1.0_windows_amd64.zip
今回は、Downloadsに保存して、作業を進めます。
解凍します。
lego.exeを使います。
legoのhelpを確認する
コマンドプロンプトでもよいですが、PowerShellを使います。
PS C:\Users\Administrator\Downloads\lego_v2.1.0_windows_amd64> .\lego.exe
NAME:
lego - Let's Encrypt client written in Go
USAGE:
lego [global options] command [command options] [arguments...]
VERSION:
dev
COMMANDS:
run Register an account, then create and install a certificate
revoke Revoke a certificate
renew Renew a certificate
dnshelp Shows additional help for the --dns global option
list Display certificates and accounts information.
help, h Shows a list of commands or help for one command
GLOBAL OPTIONS:
--domains value, -d value Add a domain to the process. Can be specified multiple times.
--server value, -s value CA hostname (and optionally :port). The server certificate must be trusted in order to avoid further modifications to the client. (default: "https://acme-v02.api.letsencrypt.org/directory")
--accept-tos, -a By setting this flag to true you indicate that you accept the current Let's Encrypt terms of service.
--email value, -m value Email used for registration and recovery contact.
--csr value, -c value Certificate signing request filename, if an external CSR is to be used.
--eab Use External Account Binding for account registration. Requires --kid and --hmac.
--kid value Key identifier from External CA. Used for External Account Binding.
--hmac value MAC key from External CA. Should be in Base64 URL Encoding without padding format. Used for External Account Binding.
--key-type value, -k value Key type to use for private keys. Supported: rsa2048, rsa4096, rsa8192, ec256, ec384. (default: "rsa2048")
--filename value (deprecated) Filename of the generated certificate.
--path value Directory to use for storing the data. (default: "/Users/teruhirokomaki/.lego")
--http Use the HTTP challenge to solve challenges. Can be mixed with other types of challenges.
--http.port value Set the port and interface to use for HTTP based challenges to listen on.Supported: interface:port or :port. (default: ":80")
--http.webroot value Set the webroot folder to use for HTTP based challenges to write directly in a file in .well-known/acme-challenge.
--http.memcached-host value Set the memcached host(s) to use for HTTP based challenges. Challenges will be written to all specified hosts.
--tls Use the TLS challenge to solve challenges. Can be mixed with other types of challenges.
--tls.port value Set the port and interface to use for TLS based challenges to listen on. Supported: interface:port or :port. (default: ":443")
--dns value Solve a DNS challenge using the specified provider. Can be mixed with other types of challenges. Run 'lego dnshelp' for help on usage.
--dns.disable-cp By setting this flag to true, disables the need to wait the propagation of the TXT record to all authoritative name servers.
--dns.resolvers value Set the resolvers to use for performing recursive DNS queries. Supported: host:port. The default is to use the system resolvers, or Google's DNS resolvers if the system's cannot be determined.
--http-timeout value Set the HTTP timeout value to a specific value in seconds. (default: 0)
--dns-timeout value Set the DNS timeout value to a specific value in seconds. Used only when performing authoritative name servers queries. (default: 10)
--pem Generate a .pem file by concatenating the .key and .crt files together.
--cert.timeout value Set the certificate timeout value to a specific value in seconds. Only used when obtaining certificates. (default: 30)
--help, -h show help
--version, -v print the version
legoのdnshelpを確認する
DNS認証で発行したいので、dnshelpを確認します。
exampleを見ると、コマンドやオプションの指定の仕方がわかります。
PS C:\Users\Administrator\Downloads\lego_v2.1.0_windows_amd64> .\lego.exe dnshelp Credentials for DNS providers must be passed through environment variables. Here is an example bash command using the CloudFlare DNS provider: $ [email protected] \ CLOUDFLARE_API_KEY=b9841238feb177a84330febba8a83208921177bffe733 \ lego --dns cloudflare --domains www.example.com --email [email protected] run Valid providers and their associated credential environment variables: acme-dns: ACME_DNS_API_BASE, ACME_DNS_STORAGE_PATH alidns: ALICLOUD_ACCESS_KEY, ALICLOUD_SECRET_KEY auroradns: AURORA_USER_ID, AURORA_KEY, AURORA_ENDPOINT azure: AZURE_CLIENT_ID, AZURE_CLIENT_SECRET, AZURE_SUBSCRIPTION_ID, AZURE_TENANT_ID, AZURE_RESOURCE_GROUP bluecat: BLUECAT_SERVER_URL, BLUECAT_USER_NAME, BLUECAT_PASSWORD, BLUECAT_CONFIG_NAME, BLUECAT_DNS_VIEW cloudflare: CLOUDFLARE_EMAIL, CLOUDFLARE_API_KEY cloudxns: CLOUDXNS_API_KEY, CLOUDXNS_SECRET_KEY conoha: CONOHA_TENANT_ID, CONOHA_API_USERNAME, CONOHA_API_PASSWORD digitalocean: DO_AUTH_TOKEN dnsimple: DNSIMPLE_EMAIL, DNSIMPLE_OAUTH_TOKEN dnsmadeeasy: DNSMADEEASY_API_KEY, DNSMADEEASY_API_SECRET dnspod: DNSPOD_API_KEY dreamhost: DREAMHOST_API_KEY duckdns: DUCKDNS_TOKEN dyn: DYN_CUSTOMER_NAME, DYN_USER_NAME, DYN_PASSWORD exec: EXEC_PATH, EXEC_MODE exoscale: EXOSCALE_API_KEY, EXOSCALE_API_SECRET, EXOSCALE_ENDPOINT fastdns: AKAMAI_HOST, AKAMAI_CLIENT_TOKEN, AKAMAI_CLIENT_SECRET, AKAMAI_ACCESS_TOKEN gandi: GANDI_API_KEY gandiv5: GANDIV5_API_KEY gcloud: GCE_PROJECT, 'Application Default Credentials', [GCE_SERVICE_ACCOUNT_FILE] glesys: GLESYS_API_USER, GLESYS_API_KEY godaddy: GODADDY_API_KEY, GODADDY_API_SECRET hostingde: HOSTINGDE_API_KEY, HOSTINGDE_ZONE_NAME httpreq: HTTPREQ_ENDPOINT, HTTPREQ_MODE, HTTPREQ_USERNAME, HTTPREQ_PASSWORD iij: IIJ_API_ACCESS_KEY, IIJ_API_SECRET_KEY, IIJ_DO_SERVICE_CODE inwx: INWX_USERNAME, INWX_PASSWORD lightsail: AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY, DNS_ZONE linode: LINODE_API_KEY linodev4: LINODE_TOKEN manual: none mydnsjp: MYDNSJP_MASTER_ID, MYDNSJP_PASSWORD namecheap: NAMECHEAP_API_USER, NAMECHEAP_API_KEY namedotcom: NAMECOM_USERNAME, NAMECOM_API_TOKEN netcup: NETCUP_CUSTOMER_NUMBER, NETCUP_API_KEY, NETCUP_API_PASSWORD nifcloud: NIFCLOUD_ACCESS_KEY_ID, NIFCLOUD_SECRET_ACCESS_KEY ns1: NS1_API_KEY otc: OTC_USER_NAME, OTC_PASSWORD, OTC_PROJECT_NAME, OTC_DOMAIN_NAME, OTC_IDENTITY_ENDPOINT ovh: OVH_ENDPOINT, OVH_APPLICATION_KEY, OVH_APPLICATION_SECRET, OVH_CONSUMER_KEY pdns: PDNS_API_KEY, PDNS_API_URL rackspace: RACKSPACE_USER, RACKSPACE_API_KEY rfc2136: RFC2136_TSIG_KEY, RFC2136_TSIG_SECRET, RFC2136_TSIG_ALGORITHM, RFC2136_NAMESERVER route53: AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY, AWS_REGION, AWS_HOSTED_ZONE_ID sakuracloud: SAKURACLOUD_ACCESS_TOKEN, SAKURACLOUD_ACCESS_TOKEN_SECRET selectel: SELECTEL_API_TOKEN stackpath: STACKPATH_CLIENT_ID, STACKPATH_CLIENT_SECRET, STACKPATH_STACK_ID transip: TRANSIP_ACCOUNT_NAME, TRANSIP_PRIVATE_KEY_PATH vegadns: SECRET_VEGADNS_KEY, SECRET_VEGADNS_SECRET, VEGADNS_URL vscale: VSCALE_API_TOKEN vultr: VULTR_API_KEY zoneee: ZONEEE_ENDPOINT, ZONEEE_API_USER, ZONEEE_API_KEY Additional configuration environment variables: alidns: ALICLOUD_POLLING_INTERVAL, ALICLOUD_PROPAGATION_TIMEOUT, ALICLOUD_TTL, ALICLOUD_HTTP_TIMEOUT auroradns: AURORA_POLLING_INTERVAL, AURORA_PROPAGATION_TIMEOUT, AURORA_TTL azure: AZURE_POLLING_INTERVAL, AZURE_PROPAGATION_TIMEOUT, AZURE_TTL, AZURE_METADATA_ENDPOINT bluecat: BLUECAT_POLLING_INTERVAL, BLUECAT_PROPAGATION_TIMEOUT, BLUECAT_TTL, BLUECAT_HTTP_TIMEOUT cloudflare: CLOUDFLARE_POLLING_INTERVAL, CLOUDFLARE_PROPAGATION_TIMEOUT, CLOUDFLARE_TTL, CLOUDFLARE_HTTP_TIMEOUT cloudxns: CLOUDXNS_POLLING_INTERVAL, CLOUDXNS_PROPAGATION_TIMEOUT, CLOUDXNS_TTL, CLOUDXNS_HTTP_TIMEOUT conoha: CONOHA_POLLING_INTERVAL, CONOHA_PROPAGATION_TIMEOUT, CONOHA_TTL, CONOHA_HTTP_TIMEOUT, CONOHA_REGION digitalocean: DO_POLLING_INTERVAL, DO_PROPAGATION_TIMEOUT, DO_TTL, DO_HTTP_TIMEOUT dnsimple: DNSIMPLE_TTL, DNSIMPLE_POLLING_INTERVAL, DNSIMPLE_PROPAGATION_TIMEOUT dnsmadeeasy: DNSMADEEASY_POLLING_INTERVAL, DNSMADEEASY_PROPAGATION_TIMEOUT, DNSMADEEASY_TTL, DNSMADEEASY_HTTP_TIMEOUT dnspod: DNSPOD_POLLING_INTERVAL, DNSPOD_PROPAGATION_TIMEOUT, DNSPOD_TTL, DNSPOD_HTTP_TIMEOUT dreamhost: DREAMHOST_POLLING_INTERVAL, DREAMHOST_PROPAGATION_TIMEOUT, DREAMHOST_HTTP_TIMEOUT duckdns: DUCKDNS_POLLING_INTERVAL, DUCKDNS_PROPAGATION_TIMEOUT, DUCKDNS_HTTP_TIMEOUT, DUCKDNS_SEQUENCE_INTERVAL dyn: DYN_POLLING_INTERVAL, DYN_PROPAGATION_TIMEOUT, DYN_TTL, DYN_HTTP_TIMEOUT exec: EXEC_POLLING_INTERVAL, EXEC_PROPAGATION_TIMEOUT exoscale: EXOSCALE_POLLING_INTERVAL, EXOSCALE_PROPAGATION_TIMEOUT, EXOSCALE_TTL, EXOSCALE_HTTP_TIMEOUT fastdns: AKAMAI_POLLING_INTERVAL, AKAMAI_PROPAGATION_TIMEOUT, AKAMAI_TTL gandi: GANDI_POLLING_INTERVAL, GANDI_PROPAGATION_TIMEOUT, GANDI_TTL, GANDI_HTTP_TIMEOUT gandiv5: GANDIV5_POLLING_INTERVAL, GANDIV5_PROPAGATION_TIMEOUT, GANDIV5_TTL, GANDIV5_HTTP_TIMEOUT gcloud: GCE_POLLING_INTERVAL, GCE_PROPAGATION_TIMEOUT, GCE_TTL glesys: GLESYS_POLLING_INTERVAL, GLESYS_PROPAGATION_TIMEOUT, GLESYS_TTL, GLESYS_HTTP_TIMEOUT godaddy: GODADDY_POLLING_INTERVAL, GODADDY_PROPAGATION_TIMEOUT, GODADDY_TTL, GODADDY_HTTP_TIMEOUT, GODADDY_SEQUENCE_INTERVAL hostingde: HOSTINGDE_POLLING_INTERVAL, HOSTINGDE_PROPAGATION_TIMEOUT, HOSTINGDE_TTL, HOSTINGDE_HTTP_TIMEOUT httpreq: HTTPREQ_POLLING_INTERVAL, HTTPREQ_PROPAGATION_TIMEOUT, HTTPREQ_HTTP_TIMEOUT iij: IIJ_POLLING_INTERVAL, IIJ_PROPAGATION_TIMEOUT, IIJ_TTL inwx: INWX_POLLING_INTERVAL, INWX_PROPAGATION_TIMEOUT, INWX_TTL, INWX_SANDBOX lightsail: LIGHTSAIL_POLLING_INTERVAL, LIGHTSAIL_PROPAGATION_TIMEOUT linode: LINODE_POLLING_INTERVAL, LINODE_TTL, LINODE_HTTP_TIMEOUT linodev4: LINODE_POLLING_INTERVAL, LINODE_TTL, LINODE_HTTP_TIMEOUT mydnsjp: MYDNSJP_PROPAGATION_TIMEOUT, MYDNSJP_POLLING_INTERVAL, MYDNSJP_HTTP_TIMEOUT namecheap: NAMECHEAP_POLLING_INTERVAL, NAMECHEAP_PROPAGATION_TIMEOUT, NAMECHEAP_TTL, NAMECHEAP_HTTP_TIMEOUT namedotcom: NAMECOM_POLLING_INTERVAL, NAMECOM_PROPAGATION_TIMEOUT, NAMECOM_TTL, NAMECOM_HTTP_TIMEOUT netcup: NETCUP_POLLING_INTERVAL, NETCUP_PROPAGATION_TIMEOUT, NETCUP_TTL, NETCUP_HTTP_TIMEOUT nifcloud: NIFCLOUD_POLLING_INTERVAL, NIFCLOUD_PROPAGATION_TIMEOUT, NIFCLOUD_TTL, NIFCLOUD_HTTP_TIMEOUT ns1: NS1_POLLING_INTERVAL, NS1_PROPAGATION_TIMEOUT, NS1_TTL, NS1_HTTP_TIMEOUT otc: OTC_POLLING_INTERVAL, OTC_PROPAGATION_TIMEOUT, OTC_TTL, OTC_HTTP_TIMEOUT ovh: OVH_POLLING_INTERVAL, OVH_PROPAGATION_TIMEOUT, OVH_TTL, OVH_HTTP_TIMEOUT pdns: PDNS_POLLING_INTERVAL, PDNS_PROPAGATION_TIMEOUT, PDNS_TTL, PDNS_HTTP_TIMEOUT rackspace: RACKSPACE_POLLING_INTERVAL, RACKSPACE_PROPAGATION_TIMEOUT, RACKSPACE_TTL, RACKSPACE_HTTP_TIMEOUT rfc2136: RFC2136_POLLING_INTERVAL, RFC2136_PROPAGATION_TIMEOUT, RFC2136_TTL, RFC2136_SEQUENCE_INTERVAL, RFC2136_DNS_TIMEOUT route53: AWS_POLLING_INTERVAL, AWS_PROPAGATION_TIMEOUT, AWS_TTL sakuracloud: SAKURACLOUD_POLLING_INTERVAL, SAKURACLOUD_PROPAGATION_TIMEOUT, SAKURACLOUD_TTL selectel: SELECTEL_BASE_URL, SELECTEL_TTL, SELECTEL_PROPAGATION_TIMEOUT, SELECTEL_POLLING_INTERVAL, SELECTEL_HTTP_TIMEOUT transip: TRANSIP_POLLING_INTERVAL, TRANSIP_PROPAGATION_TIMEOUT, TRANSIP_TTL stackpath: STACKPATH_POLLING_INTERVAL, STACKPATH_PROPAGATION_TIMEOUT, STACKPATH_TTL vegadns: VEGADNS_POLLING_INTERVAL, VEGADNS_PROPAGATION_TIMEOUT, VEGADNS_TTL vscale: VSCALE_BASE_URL, VSCALE_TTL, VSCALE_PROPAGATION_TIMEOUT, VSCALE_POLLING_INTERVAL, VSCALE_HTTP_TIMEOUT vultr: VULTR_POLLING_INTERVAL, VULTR_PROPAGATION_TIMEOUT, VULTR_TTL, VULTR_HTTP_TIMEOUT zoneee: ZONEEE_POLLING_INTERVAL, ZONEEE_PROPAGATION_TIMEOUT, ZONEEE_HTTP_TIMEOUT For a more detailed explanation of a DNS provider's credential variables, please consult their online documentation.
コマンドを実行する
今回は、マニュアルでTXTレコードを設定したいので、以下のようなオプションで実行します。
PS C:\Users\Administrator\Downloads\lego_v2.1.0_windows_amd64> .\lego.exe --dns manual --domains demo.frudens.app --email [email protected] run
コマンドを実行すると以下のようになります。
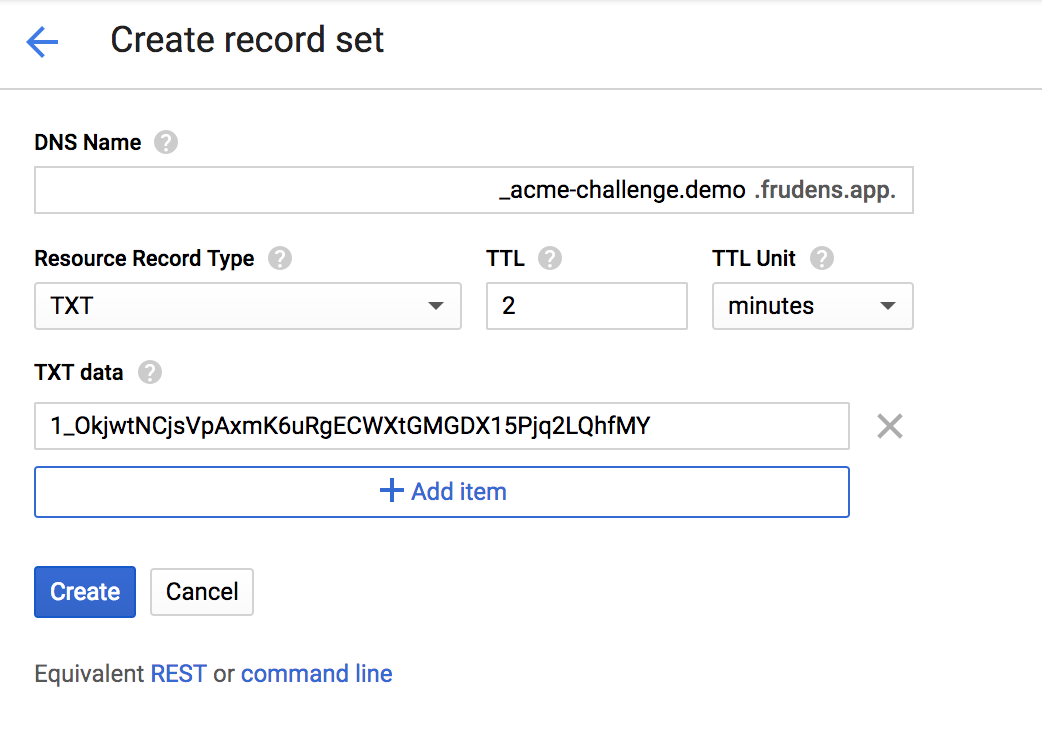
PS C:\Users\Administrator\Downloads\lego_v2.1.0_windows_amd64> .\lego.exe --dns manual --domains demo.frudens.app --email [email protected] run 2019/01/30 13:54:59 No key found for account [email protected]. Generating a curve P384 EC key. 2019/01/30 13:54:59 Saved key to C:\Users\Administrator\Downloads\lego_v2.1.0_windows_amd64\.lego\accounts\acme-v02.api.letsencrypt.org\[email protected]\keys\[email protected] ey 2019/01/30 13:55:00 Please review the TOS at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf Do you accept the TOS? Y/n 2019/01/30 13:55:06 [INFO] acme: Registering account for [email protected] !!!! HEADS UP !!!! Your account credentials have been saved in your Let's Encrypt configuration directory at "C:\Users\Administrator\Downloads\lego_v2.1.0_windows_amd64\.lego\accounts". You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained from Let's Encrypt so making regular backups of this folder is ideal.2019/01/30 13:55:07 [INFO] [demo.frudens.app] acme: Obtaining bundled SAN certificate 2019/01/30 13:55:08 [INFO] [demo.frudens.app] AuthURL: https://acme-v02.api.letsencrypt.org/acme/authz/_pjQu86-vdFHMiOiM-zwJ7W2l2Lildp_I48Pyq49kiQ 2019/01/30 13:55:08 [INFO] [demo.frudens.app] acme: Could not find solver for: tls-alpn-01 2019/01/30 13:55:08 [INFO] [demo.frudens.app] acme: Could not find solver for: http-01 2019/01/30 13:55:08 [INFO] [demo.frudens.app] acme: use dns-01 solver 2019/01/30 13:55:08 [INFO] [demo.frudens.app] acme: Preparing to solve DNS-01 lego: Please create the following TXT record in your frudens.app. zone: _acme-challenge.demo.frudens.app. 120 IN TXT "1_OkjwtNCjsVpAxmK6uRgECWXtGMGDX15Pjq2LQhfMY" lego: Press 'Enter' when you are done
上にも出力されてますが、以下の部分から分かる通り「TXTレコードに追加してエンターを叩いてください。」とのことです。
ということで、PowerShellはそのままで、TXTレコードに追加します。
lego: Please create the following TXT record in your frudens.app. zone: _acme-challenge.demo.frudens.app. 120 IN TXT "1_OkjwtNCjsVpAxmK6uRgECWXtGMGDX15Pjq2LQhfMY" lego: Press 'Enter' when you are done
TXTレコードに追加する
私は、GCP Cloud DNSを使っているので、このようにTXTレコードを追加します。
nslookupやdigでTXTレコードを確認する
以下のコマンドにて確認します。
(以下は、手元のLinuxマシンで確認した際のコマンドです。)
nslookup
(ins) ~ $ nslookup -type=TXT _acme-challenge.demo.frudens.app. Server: 192.168.100.1 Address: 192.168.100.1#53 Non-authoritative answer: _acme-challenge.demo.frudens.app text = "1_OkjwtNCjsVpAxmK6uRgECWXtGMGDX15Pjq2LQhfMY" Authoritative answers can be found from: frudens.app nameserver = ns-cloud-a2.googledomains.com. frudens.app nameserver = ns-cloud-a3.googledomains.com. frudens.app nameserver = ns-cloud-a4.googledomains.com. frudens.app nameserver = ns-cloud-a1.googledomains.com. ns-cloud-a1.googledomains.com internet address = 216.239.32.106 ns-cloud-a2.googledomains.com internet address = 216.239.34.106 ns-cloud-a3.googledomains.com internet address = 216.239.36.106 ns-cloud-a4.googledomains.com internet address = 216.239.38.106 ns-cloud-a1.googledomains.com has AAAA address 2001:4860:4802:32::6a ns-cloud-a2.googledomains.com has AAAA address 2001:4860:4802:34::6a ns-cloud-a3.googledomains.com has AAAA address 2001:4860:4802:36::6a ns-cloud-a4.googledomains.com has AAAA address 2001:4860:4802:38::6a
dig
(cmd) ~ $ dig +noedns _acme-challenge.demo.frudens.app. TXT ; <<>> DiG 9.10.6 <<>> +noedns _acme-challenge.demo.frudens.app. TXT ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 31238 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 4, ADDITIONAL: 8 ;; QUESTION SECTION: ;_acme-challenge.demo.frudens.app. IN TXT ;; ANSWER SECTION: _acme-challenge.demo.frudens.app. 69 IN TXT "1_OkjwtNCjsVpAxmK6uRgECWXtGMGDX15Pjq2LQhfMY" ;; AUTHORITY SECTION: frudens.app. 129 IN NS ns-cloud-a2.googledomains.com. frudens.app. 129 IN NS ns-cloud-a3.googledomains.com. frudens.app. 129 IN NS ns-cloud-a4.googledomains.com. frudens.app. 129 IN NS ns-cloud-a1.googledomains.com. ;; ADDITIONAL SECTION: ns-cloud-a1.googledomains.com. 217045 IN A 216.239.32.106 ns-cloud-a2.googledomains.com. 221622 IN A 216.239.34.106 ns-cloud-a3.googledomains.com. 129119 IN A 216.239.36.106 ns-cloud-a4.googledomains.com. 29107 IN A 216.239.38.106 ns-cloud-a1.googledomains.com. 227739 IN AAAA 2001:4860:4802:32::6a ns-cloud-a2.googledomains.com. 224186 IN AAAA 2001:4860:4802:34::6a ns-cloud-a3.googledomains.com. 217045 IN AAAA 2001:4860:4802:36::6a ns-cloud-a4.googledomains.com. 208722 IN AAAA 2001:4860:4802:38::6a ;; Query time: 49 msec ;; SERVER: 192.168.100.1#53(192.168.100.1) ;; WHEN: Wed Jan 30 23:05:44 JST 2019 ;; MSG SIZE rcvd: 403
PowerShellでエンターをターンする
TXTレコードが確認できたら、あとはエンターをターンして完了です。
lego: Press 'Enter' when you are done 2019/01/30 14:09:06 [INFO] [demo.frudens.app] acme: Trying to solve DNS-01 2019/01/30 14:09:06 [INFO] [demo.frudens.app] acme: Checking DNS record propagation using [google-public-dns-a.google.com:53 google-public-dns-b.google.com:53] 2019/01/30 14:09:06 [INFO] Wait for propagation [timeout: 1m0s, interval: 2s] 2019/01/30 14:09:06 [INFO] nonce error retry: acme: error: 400 :: POST :: https://acme-v02.api.letsencrypt.org/acme/challenge/_pjQu86-vdFHMiOiM-zwJ7W2l2Lildp_I48Pyq49kiQ/12053229430 :: urn:iet f:params:acme:error:badNonce :: JWS has an invalid anti-replay nonce: "iA-FkWTlT1EFOHFUtahmSy2ZgoCjW7tlkbZOkAUVv-E", url: 2019/01/30 14:09:12 [INFO] [demo.frudens.app] The server validated our request 2019/01/30 14:09:12 [INFO] [demo.frudens.app] acme: Cleaning DNS-01 challenge lego: You can now remove this TXT record from your frudens.app. zone: _acme-challenge.demo.frudens.app. 120 IN TXT "..." 2019/01/30 14:09:12 [INFO] [demo.frudens.app] acme: Validations succeeded; requesting certificates 2019/01/30 14:09:13 [INFO] [demo.frudens.app] Server responded with a certificate.
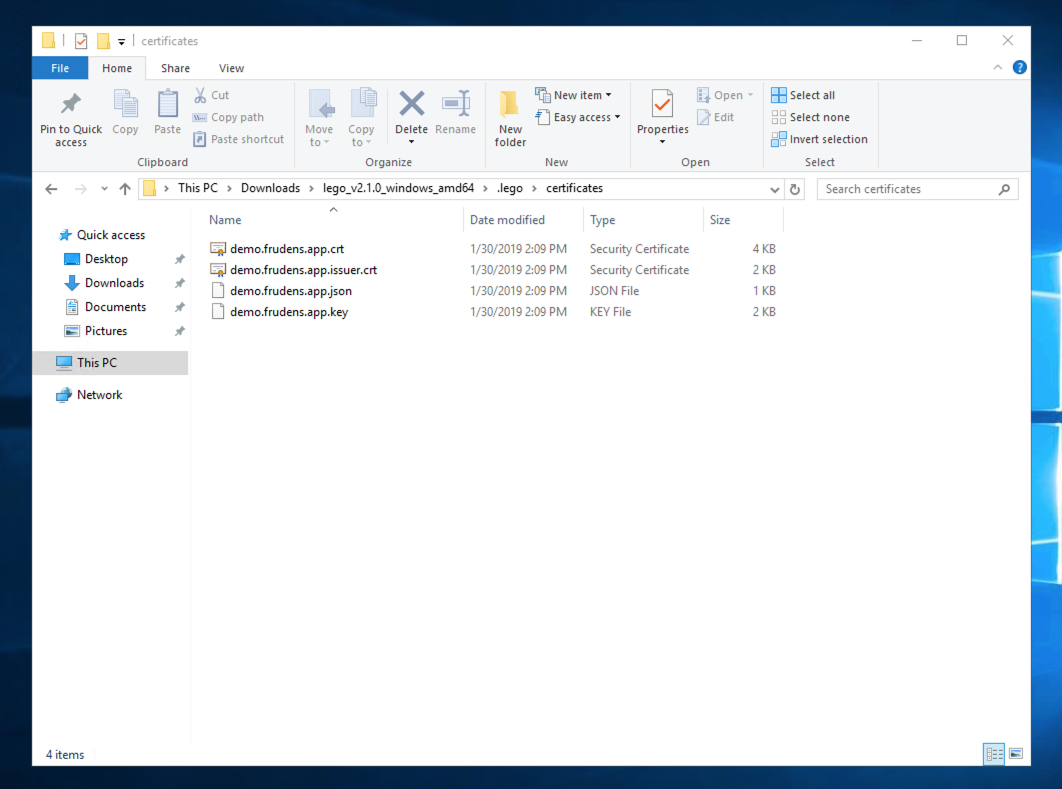
証明書が生成される
以下のフォルダに生成されます。
PS C:\Users\Administrator\Downloads\lego_v2.1.0_windows_amd64> cd .\.lego\certificates\
PS C:\Users\Administrator\Downloads\lego_v2.1.0_windows_amd64\.lego\certificates> ls
Directory: C:\Users\Administrator\Downloads\lego_v2.1.0_windows_amd64\.lego\certificates
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/30/2019 2:09 PM 3563 demo.frudens.app.crt
-a---- 1/30/2019 2:09 PM 1648 demo.frudens.app.issuer.crt
-a---- 1/30/2019 2:09 PM 237 demo.frudens.app.json
-a---- 1/30/2019 2:09 PM 1675 demo.frudens.app.key
証明書をFileMaker Serverにインポートする
fmsadminコマンドでFileMaker Serverにインポートします。
Admin Consoleからでもインポートできますので、お好きな方でインポートしてください。
legoでrenewすることや、FileMaker Serverで証明書を再インポートすることなどを考えると、fmsadminコマンドに慣れておくことをオススメします。
PowerShellではなく、コマンドプロンプトを起動して、以下のコマンドを実行します。
すでに、証明書が設定されている場合、現在の証明書を削除してから、インポートする必要があります。
C:\Users\Administrator>fmsadmin -u user -p password certificate import C:\Users\Administrator\Downloads\lego_v2.1.0_windows_amd64\.lego\certificates\demo.frudens.app.crt --keyfile C:\Users\Administrator\Downloads\lego_v2.1.0_windows_amd64\.lego\certificates\demo.frudens.app.key --intermediateca C:\Users\Administrator\Downloads\lego_v2.1.0_windows_amd64\.lego\certificates\demo.frudens.app.issuer.crt fmsadmin: really import certificate? (y, n) (Warning: server needs to be restarted) y Restart the FileMaker Server service to apply the change.
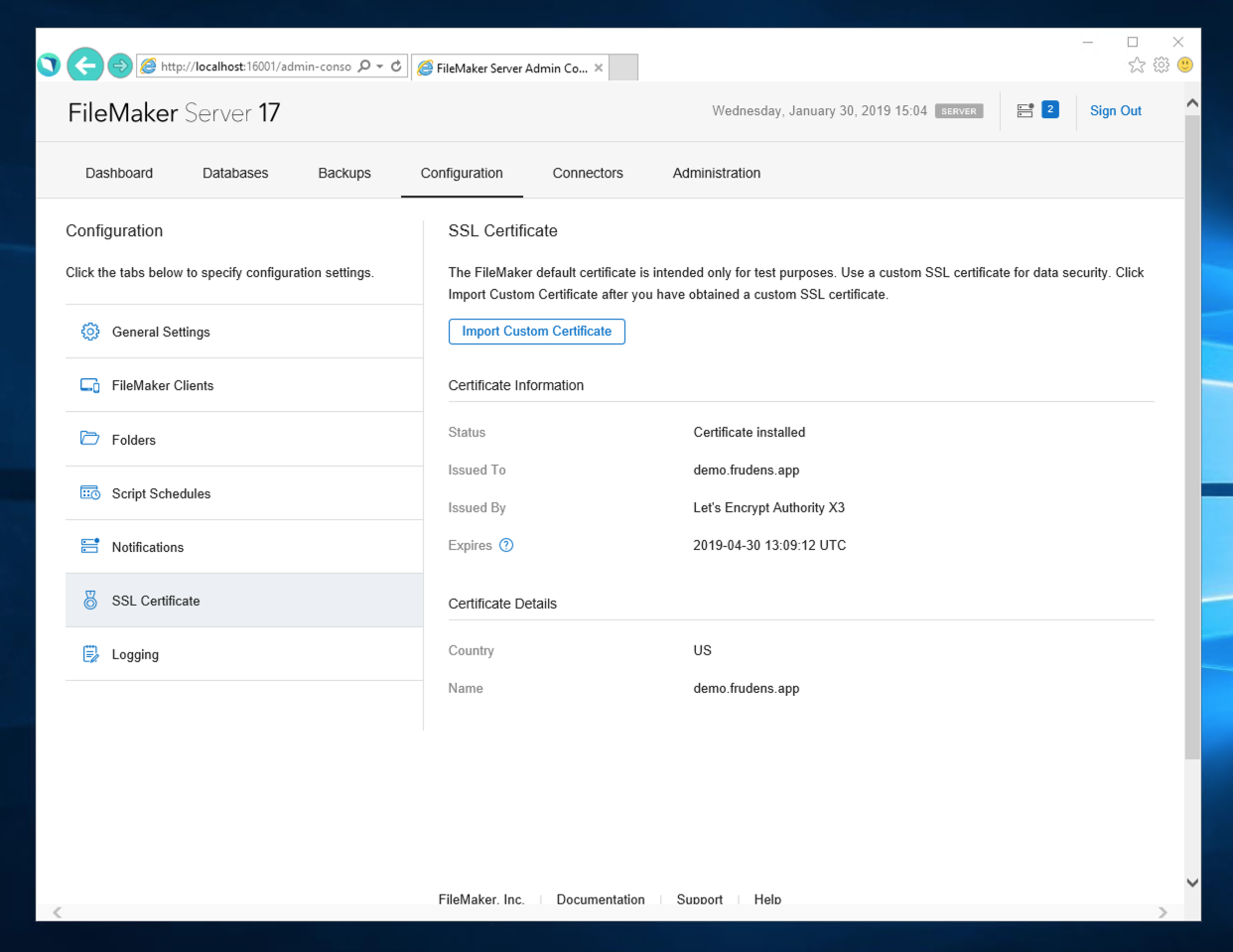
FileMaker ServerのServiceをRestartして確認する
Admin Consoleで確認します。
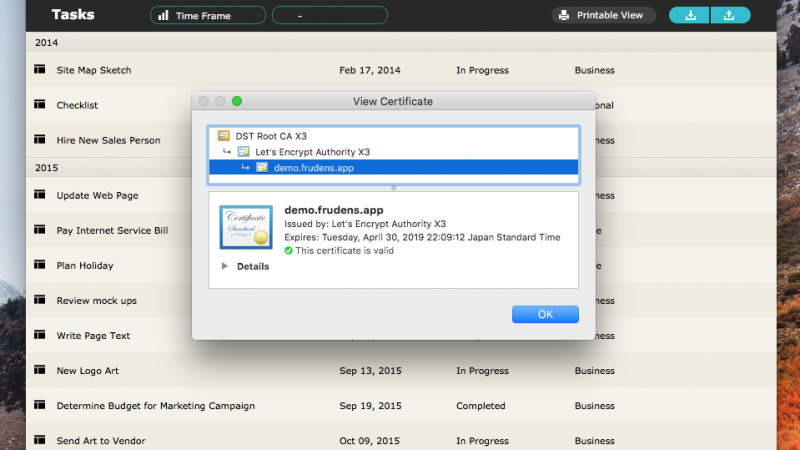
無事インポートされています。
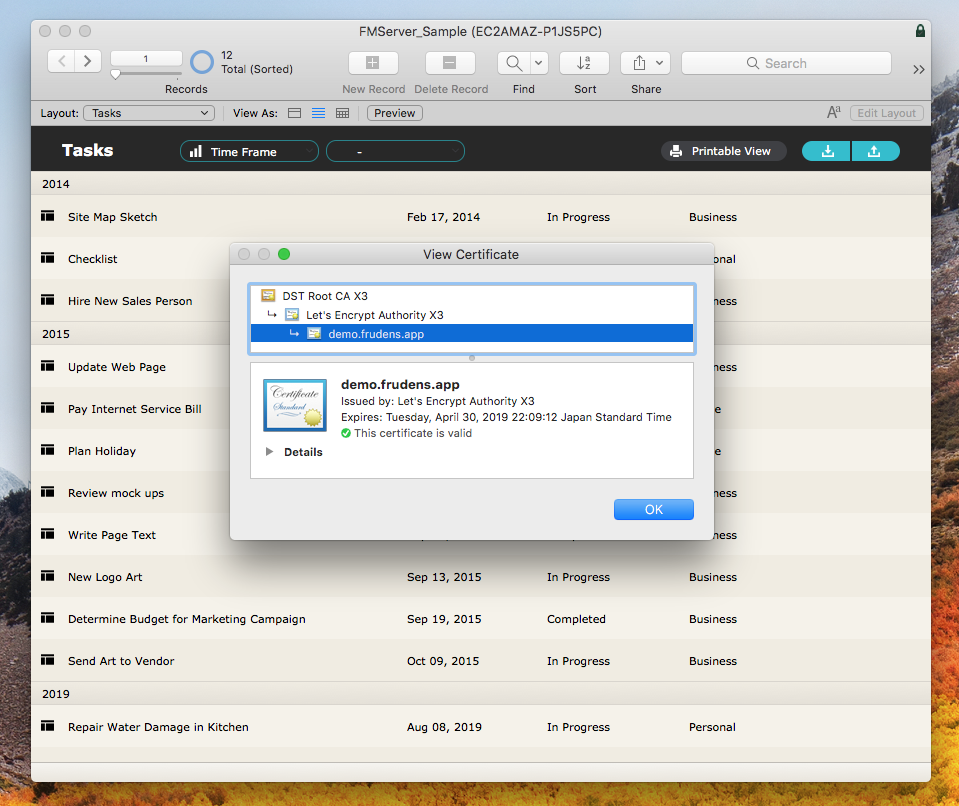
FileMaker Pro 17 Advancedにて、確認します。
あとがき
DNS認証のため、ポートはあけなくても大丈夫なところがよいですね。
Let’s Encryptは90日で期限がきれますので、上記のコマンドをバッチフィルにして、60日間隔などで定期的に実行してください。
以前、別のクライアントを使って挑戦したことを記事にしております。
ご興味が有る方は、ご覧頂ければと思います。
FileMaker ServerにLet’s EncryptのSSL証明書を設定する
Windows ServerでLet’s EncryptのDNS認証を試みて失敗した話
CLIが好きなため「Windows ServerにSSHでアクセスしたい。」と思っており、調べてたところ以下のリポジトリを見つけました。
https://github.com/PowerShell/Win32-OpenSSH
インストールや設定が非常に簡単にでき、快適にSSHできるようになりました。
デフォルトのシェルはコマンドプロントですが…
こちらも、記事にしたいと思います。
